#How To Prevent Unauthorized Computer Access
Explore tagged Tumblr posts
Text
How to Protect Your Computer from Unauthorized Access?
Today, we live our lives online and on gadgets that are connected to the internet. We use the internet to do research, shop, bank, do assignments, play games, and connect with loved ones through social media. Because of this, our gadgets are filled with a
Continue reading How to Protect Your Computer from Unauthorized Access?
#Hackers#How To Prevent Unauthorized Computer Access#How To Protect Your Computer From Unauthorized Access#How To Save From Hacking#Methods For Preventing Unwanted Access To Your Computer#Protect Your Computer From Viruses
0 notes
Text
Cleantech has an enshittification problem

On July 14, I'm giving the closing keynote for the fifteenth HACKERS ON PLANET EARTH, in QUEENS, NY. Happy Bastille Day! On July 20, I'm appearing in CHICAGO at Exile in Bookville.

EVs won't save the planet. Ultimately, the material bill for billions of individual vehicles and the unavoidable geometry of more cars-more traffic-more roads-greater distances-more cars dictate that the future of our cities and planet requires public transit – lots of it.
But no matter how much public transit we install, there's always going to be some personal vehicles on the road, and not just bikes, ebikes and scooters. Between deliveries, accessibility, and stubbornly low-density regions, there's going to be a lot of cars, vans and trucks on the road for the foreseeable future, and these should be electric.
Beyond that irreducible minimum of personal vehicles, there's the fact that individuals can't install their own public transit system; in places that lack the political will or means to create working transit, EVs are a way for people to significantly reduce their personal emissions.
In policy circles, EV adoption is treated as a logistical and financial issue, so governments have focused on making EVs affordable and increasing the density of charging stations. As an EV owner, I can affirm that affordability and logistics were important concerns when we were shopping for a car.
But there's a third EV problem that is almost entirely off policy radar: enshittification.
An EV is a rolling computer in a fancy case with a squishy person inside of it. While this can sound scary, there are lots of cool implications for this. For example, your EV could download your local power company's tariff schedule and preferentially charge itself when the rates are lowest; they could also coordinate with the utility to reduce charging when loads are peaking. You can start them with your phone. Your repair technician can run extensive remote diagnostics on them and help you solve many problems from the road. New features can be delivered over the air.
That's just for starters, but there's so much more in the future. After all, the signal virtue of a digital computer is its flexibility. The only computer we know how to make is the Turing complete, universal, Von Neumann machine, which can run every valid program. If a feature is computationally tractable – from automated parallel parking to advanced collision prevention – it can run on a car.
The problem is that this digital flexibility presents a moral hazard to EV manufacturers. EVs are designed to make any kind of unauthorized, owner-selected modification into an IP rights violation ("IP" in this case is "any law that lets me control the conduct of my customers or competitors"):
https://locusmag.com/2020/09/cory-doctorow-ip/
EVs are also designed so that the manufacturer can unilaterally exert control over them or alter their operation. EVs – even more than conventional vehicles – are designed to be remotely killswitched in order to help manufacturers and dealers pressure people into paying their car notes on time:
https://pluralistic.net/2023/07/24/rent-to-pwn/#kitt-is-a-demon
Manufacturers can reach into your car and change how much of your battery you can access:
https://pluralistic.net/2023/07/28/edison-not-tesla/#demon-haunted-world
They can lock your car and have it send its location to a repo man, then greet him by blinking its lights, honking its horn, and pulling out of its parking space:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
And of course, they can detect when you've asked independent mechanic to service your car and then punish you by degrading its functionality:
https://www.repairerdrivennews.com/2024/06/26/two-of-eight-claims-in-tesla-anti-trust-lawsuit-will-move-forward/
This is "twiddling" – unilaterally and irreversibly altering the functionality of a product or service, secure in the knowledge that IP law will prevent anyone from twiddling back by restoring the gadget to a preferred configuration:
https://pluralistic.net/2023/02/19/twiddler/
The thing is, for an EV, twiddling is the best case scenario. As bad as it is for the company that made your EV to change how it works whenever they feel like picking your pocket, that's infinitely preferable to the manufacturer going bankrupt and bricking your car.
That's what just happened to owners of Fisker EVs, cars that cost $40-70k. Cars are long-term purchases. An EV should last 12-20 years, or even longer if you pay to swap the battery pack. Fisker was founded in 2016 and shipped its first Ocean SUV in 2023. The company is now bankrupt:
https://insideevs.com/news/723669/fisker-inc-bankruptcy-chapter-11-official/
Fisker called its vehicles "software-based cars" and they weren't kidding. Without continuous software updates and server access, those Fisker Ocean SUVs are turning into bricks. What's more, the company designed the car from the ground up to make any kind of independent service and support into a felony, by wrapping the whole thing in overlapping layers of IP. That means that no one can step in with a module that jailbreaks the Fisker and drops in an alternative firmware that will keep the fleet rolling.
This is the third EV risk – not just finance, not just charger infrastructure, but the possibility that any whizzy, cool new EV company will go bust and brick your $70k cleantech investment, irreversibly transforming your car into 5,500 lb worth of e-waste.
This confers a huge advantage onto the big automakers like VW, Kia, Ford, etc. Tesla gets a pass, too, because it achieved critical mass before people started to wise up to the risk of twiddling and bricking. If you're making a serious investment in a product you expect to use for 20 years, are you really gonna buy it from a two-year old startup with six months' capital in the bank?
The incumbency advantage here means that the big automakers won't have any reason to sink a lot of money into R&D, because they won't have to worry about hungry startups with cool new ideas eating their lunches. They can maintain the cozy cartel that has seen cars stagnate for decades, with the majority of "innovation" taking the form of shitty, extractive and ill-starred ideas like touchscreen controls and an accelerator pedal that you have to rent by the month:
https://www.theverge.com/2022/11/23/23474969/mercedes-car-subscription-faster-acceleration-feature-price
Put that way, it's clear that this isn't an EV problem, it's a cleantech problem. Cleantech has all the problems of EVs: it requires a large capital expenditure, it will be "smart," and it is expected to last for decades. That's rooftop solar, heat-pumps, smart thermostat sensor arrays, and home storage batteries.
And just as with EVs, policymakers have focused on infrastructure and affordability without paying any attention to the enshittification risks. Your rooftop solar will likely be controlled via a Solaredge box – a terrible technology that stops working if it can't reach the internet for a protracted period (that's right, your home solar stops working if the grid fails!).
I found this out the hard way during the covid lockdowns, when Solaredge terminated its 3G cellular contract and notified me that I would have to replace the modem in my system or it would stop working. This was at the height of the supply-chain crisis and there was a long waiting list for any replacement modems, with wifi cards (that used your home internet rather than a cellular connection) completely sold out for most of a year.
There are good reasons to connect rooftop solar arrays to the internet – it's not just so that Solaredge can enshittify my service. Solar arrays that coordinate with the grid can make it much easier and safer to manage a grid that was designed for centralized power production and is being retrofitted for distributed generation, one roof at a time.
But when the imperatives of extraction and efficiency go to war, extraction always wins. After all, the Solaredge system is already in place and solar installers are largely ignorant of, and indifferent to, the reasons that a homeowner might want to directly control and monitor their system via local controls that don't roundtrip through the cloud.
Somewhere in the hindbrain of any prospective solar purchaser is the experience with bricked and enshittified "smart" gadgets, and the knowledge that anything they buy from a cool startup with lots of great ideas for improving production, monitoring, and/or costs poses the risk of having your 20 year investment bricked after just a few years – and, thanks to the extractive imperative, no one will be able to step in and restore your ex-solar array to good working order.
I make the majority of my living from books, which means that my pay is very "lumpy" – I get large sums when I publish a book and very little in between. For many years, I've used these payments to make big purchases, rather than financing them over long periods where I can't predict my income. We've used my book payments to put in solar, then an induction stove, then a battery. We used one to buy out the lease on our EV. And just a month ago, we used the money from my upcoming Enshittification book to put in a heat pump (with enough left over to pay for a pair of long-overdue cataract surgeries, scheduled for the fall).
When we started shopping for heat pumps, it was clear that this was a very exciting sector. First of all, heat pumps are kind of magic, so efficient and effective it's almost surreal. But beyond the basic tech – which has been around since the late 1940s – there is a vast ferment of cool digital features coming from exciting and innovative startups.
By nature, I'm the kid of person who likes these digital features. I started out as a computer programmer, and while I haven't written production code since the previous millennium, I've been in and around the tech industry for my whole adult life. But when it came time to buy a heat-pump – an investment that I expected to last for 20 years or more – there was no way I was going to buy one of these cool new digitally enhanced pumps, no matter how much the reviewers loved them. Sure, they'd work well, but it's precisely because I'm so knowledgeable about high tech that I could see that they would fail very, very badly.
You may think EVs are bullshit, and they are – though there will always be room for some personal vehicles, and it's better for people in transit deserts to drive EVs than gas-guzzlers. You may think rooftop solar is a dead-end and be all-in on utility scale solar (I think we need both, especially given the grid-disrupting extreme climate events on our horizon). But there's still a wide range of cleantech – induction tops, heat pumps, smart thermostats – that are capital intensive, have a long duty cycle, and have good reasons to be digitized and networked.
Take home storage batteries: your utility can push its rate card to your battery every time they change their prices, and your battery can use that information to decide when to let your house tap into the grid, and when to switch over to powering your home with the solar you've stored up during the day. This is a very old and proven pattern in tech: the old Fidonet BBS network used a version of this, with each BBS timing its calls to other nodes to coincide with the cheapest long-distance rates, so that messages for distant systems could be passed on:
https://en.wikipedia.org/wiki/FidoNet
Cleantech is a very dynamic sector, even if its triumphs are largely unheralded. There's a quiet revolution underway in generation, storage and transmission of renewable power, and a complimentary revolution in power-consumption in vehicles and homes:
https://pluralistic.net/2024/06/12/s-curve/#anything-that-cant-go-on-forever-eventually-stops
But cleantech is too important to leave to the incumbents, who are addicted to enshittification and planned obsolescence. These giant, financialized firms lack the discipline and culture to make products that have the features – and cost savings – to make them appealing to the very wide range of buyers who must transition as soon as possible, for the sake of the very planet.
It's not enough for our policymakers to focus on financing and infrastructure barriers to cleantech adoption. We also need a policy-level response to enshittification.
Ideally, every cleantech device would be designed so that it was impossible to enshittify – which would also make it impossible to brick:
Based on free software (best), or with source code escrowed with a trustee who must release the code if the company enters administration (distant second-best);
All patents in a royalty-free patent-pool (best); or in a trust that will release them into a royalty-free pool if the company enters administration (distant second-best);
No parts-pairing or other DRM permitted (best); or with parts-pairing utilities available to all parties on a reasonable and non-discriminatory basis (distant second-best);
All diagnostic and error codes in the public domain, with all codes in the clear within the device (best); or with decoding utilities available on demand to all comers on a reasonable and non-discriminatory basis (distant second-best).
There's an obvious business objection to this: it will reduce investment in innovative cleantech because investors will perceive these restrictions as limits on the expected profits of their portfolio companies. It's true: these measures are designed to prevent rent-extraction and other enshittificatory practices by cleantech companies, and to the extent that investors are counting on enshittification rents, this might prevent them from investing.
But that has to be balanced against the way that a general prohibition on enshittificatory practices will inspire consumer confidence in innovative and novel cleantech products, because buyers will know that their investments will be protected over the whole expected lifespan of the product, even if the startup goes bust (nearly every startup goes bust). These measures mean that a company with a cool product will have a much larger customer-base to sell to. Those additional sales more than offset the loss of expected revenue from cheating and screwing your customers by twiddling them to death.
There's also an obvious legal objection to this: creating these policies will require a huge amount of action from Congress and the executive branch, a whole whack of new rules and laws to make them happen, and each will attract court-challenges.
That's also true, though it shouldn't stop us from trying to get legal reforms. As a matter of public policy, it's terrible and fucked up that companies can enshittify the things we buy and leave us with no remedy.
However, we don't have to wait for legal reform to make this work. We can take a shortcut with procurement – the things governments buy with public money. The feds, the states and localities buy a lot of cleantech: for public facilities, for public housing, for public use. Prudent public policy dictates that governments should refuse to buy any tech unless it is designed to be enshittification-resistant.
This is an old and honorable tradition in policymaking. Lincoln insisted that the rifles he bought for the Union Army come with interoperable tooling and ammo, for obvious reasons. No one wants to be the Commander in Chief who shows up on the battlefield and says, "Sorry, boys, war's postponed, our sole supplier decided to stop making ammunition."
By creating a market for enshittification-proof cleantech, governments can ensure that the public always has the option of buying an EV that can't be bricked even if the maker goes bust, a heat-pump whose digital features can be replaced or maintained by a third party of your choosing, a solar controller that coordinates with the grid in ways that serve their owners – not the manufacturers' shareholders.
We're going to have to change a lot to survive the coming years. Sure, there's a lot of scary ways that things can go wrong, but there's plenty about our world that should change, and plenty of ways those changes could be for the better. It's not enough for policymakers to focus on ensuring that we can afford to buy whatever badly thought-through, extractive tech the biggest companies want to foist on us – we also need a focus on making cleantech fit for purpose, truly smart, reliable and resilient.

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/06/26/unplanned-obsolescence/#better-micetraps

Image: 臺灣古寫真上色 (modified) https://commons.wikimedia.org/wiki/File:Raid_on_Kagi_City_1945.jpg
Grendelkhan (modified) https://commons.wikimedia.org/wiki/File:Ground_mounted_solar_panels.gk.jpg
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#procurement#cleantech#evs#solar#solarpunk#policy#copyfight#copyright#felony contempt of business model#floss#free software#open source#oss#dmca 1201#interoperability#adversarial interoperability#solarization#electrification#enshittification#innovation#incumbency#climate#climate emergency
433 notes
·
View notes
Text
Democrats on the Senate Intelligence Committee are demanding answers after they say President Donald Trump gave Elon Musk's staff access to sensitive and classified government information
WASHINGTON -- Democrats on the Senate Intelligence Committee are demanding answers after they say President Donald Trump gave billionaire Elon Musk and his staff access to sensitive data and classified secrets as part of their work to overhaul the federal government.
The lawmakers on Wednesday wrote to Susie Wiles, Trump's chief of staff, and asked what security precautions had been taken to prevent unauthorized leaks of information by staff at the Department of Government Efficiency, known as DOGE. Trump tapped Musk to run the taskforce, which has quickly gotten to work dismantling whole agencies of the federal government.
As part of that effort, Musk and his staff have gained access to computer systems that the senators say contain potentially sensitive medical and financial information about millions of Americans as well as federal payroll information, classified documents, information from foreign intelligence partners and the identities of undercover agents and intelligence sources.
In the letter, the senators warned that national security and the personal privacy of Americans could be at risk if the information is mishandled — intentionally or through negligence. They ask whether Musk's team has met with U.S. intelligence officials to discuss how to reduce the chances of the data being misused and what steps to take to protect classified information, such as the identities of CIA informants or the actions of overseas intelligence operatives.
Such information would be highly valuable to the spy agencies of Russia, China, Iran and other nations, and its loss could put lives at risk while undermining efforts to prevent terrorism and other threats to the U.S., the senators wrote.
78 notes
·
View notes
Text
Smart Switchgear in 2025: What Electrical Engineers Need to Know

In the fast-evolving world of electrical infrastructure, smart switchgear is no longer a futuristic concept — it’s the new standard. As we move through 2025, the integration of intelligent systems into traditional switchgear is redefining how engineers design, monitor, and maintain power distribution networks.
This shift is particularly crucial for electrical engineers, who are at the heart of innovation in sectors like manufacturing, utilities, data centers, commercial construction, and renewable energy.
In this article, we’ll break down what smart switchgear means in 2025, the technologies behind it, its benefits, and what every electrical engineer should keep in mind.
What is Smart Switchgear?
Smart switchgear refers to traditional switchgear (devices used for controlling, protecting, and isolating electrical equipment) enhanced with digital technologies, sensors, and communication modules that allow:
Real-time monitoring
Predictive maintenance
Remote operation and control
Data-driven diagnostics and performance analytics
This transformation is powered by IoT (Internet of Things), AI, cloud computing, and edge devices, which work together to improve reliability, safety, and efficiency in electrical networks.
Key Innovations in Smart Switchgear (2025 Edition)
1. IoT Integration
Smart switchgear is equipped with intelligent sensors that collect data on temperature, current, voltage, humidity, and insulation. These sensors communicate wirelessly with central systems to provide real-time status and alerts.
2. AI-Based Predictive Maintenance
Instead of traditional scheduled inspections, AI algorithms can now predict component failure based on usage trends and environmental data. This helps avoid downtime and reduces maintenance costs.
3. Cloud Connectivity
Cloud platforms allow engineers to remotely access switchgear data from any location. With user-friendly dashboards, they can visualize key metrics, monitor health conditions, and set thresholds for automated alerts.
4. Cybersecurity Enhancements
As devices get connected to networks, cybersecurity becomes crucial. In 2025, smart switchgear is embedded with secure communication protocols, access control layers, and encrypted data streams to prevent unauthorized access.
5. Digital Twin Technology
Some manufacturers now offer a digital twin of the switchgear — a virtual replica that updates in real-time. Engineers can simulate fault conditions, test load responses, and plan future expansions without touching the physical system.
Benefits for Electrical Engineers
1. Operational Efficiency
Smart switchgear reduces manual inspections and allows remote diagnostics, leading to faster response times and reduced human error.
2. Enhanced Safety
Early detection of overload, arc flash risks, or abnormal temperatures enhances on-site safety, especially in high-voltage environments.
3. Data-Driven Decisions
Real-time analytics help engineers understand load patterns and optimize distribution for efficiency and cost savings.
4. Seamless Scalability
Modular smart systems allow for quick expansion of power infrastructure, particularly useful in growing industrial or smart city projects.
Applications Across Industries
Manufacturing Plants — Monitor energy use per production line
Data Centers — Ensure uninterrupted uptime and cooling load balance
Commercial Buildings — Integrate with BMS (Building Management Systems)
Renewable Energy Projects — Balance grid load from solar or wind sources
Oil & Gas Facilities — Improve safety and compliance through monitoring
What Engineers Need to Know Moving Forward
1. Stay Updated with IEC & IEEE Standards
Smart switchgear must comply with global standards. Engineers need to be familiar with updates related to IEC 62271, IEC 61850, and IEEE C37 series.
2. Learn Communication Protocols
Proficiency in Modbus, DNP3, IEC 61850, and OPC UA is essential to integrating and troubleshooting intelligent systems.
3. Understand Lifecycle Costing
Smart switchgear might have a higher upfront cost but offers significant savings in maintenance, energy efficiency, and downtime over its lifespan.
4. Collaborate with IT Teams
The line between electrical and IT is blurring. Engineers should work closely with cybersecurity and cloud teams for seamless, secure integration.
Conclusion
Smart switchgear is reshaping the way electrical systems are built and managed in 2025. For electrical engineers, embracing this innovation isn’t just an option — it’s a career necessity.
At Blitz Bahrain, we specialize in providing cutting-edge switchgear solutions built for the smart, digital future. Whether you’re an engineer designing the next big project or a facility manager looking to upgrade existing systems, we’re here to power your progress.
#switchgear#panel#manufacturer#bahrain25#electrical supplies#electrical equipment#electrical engineers#electrical
6 notes
·
View notes
Text
Undress AI: The Future of Digital Transformation in Image Manipulation
Brian

Introduction to Undress AI
Undress AI has become a prominent tool in the world of image manipulation, offering a unique ability to reveal hidden details in images. With advanced algorithms, this technology can "undress" individuals in images, providing an experience that captures the imagination. Whether for personal use or professional entertainment, the ability to undress AI offers users a whole new realm of possibilities when it comes to digital images.
How Undress AI Works
The process of undressing someone with AI is straightforward. The first step is to upload an image, and from there, the AI system takes over. It uses sophisticated algorithms to analyze the image and remove clothing, revealing hidden details of the individual in the picture. This happens quickly and with a high level of accuracy, making it an appealing tool for those interested in digital image manipulation.
Technology Behind Undress AI
The magic of undress AI lies in its technology. Advanced deep learning models and computer vision techniques enable the software to process images in ways that seem almost magical. By identifying key features of clothing and human anatomy, the AI can seamlessly generate realistic results. The system doesn’t just remove clothing; it enhances the overall visual experience by maintaining the integrity of the subject's proportions.
Privacy and Security Considerations
Privacy is a top priority when using undress AI. The platform uses AES-256 encryption, ensuring that user data is secure throughout the process. This means that all images are protected, preventing unauthorized access and maintaining confidentiality. For those who are concerned about privacy, rest assured that this system provides a secure environment for your images and data.
Different Pricing Plans for Everyone
Undress AI offers a variety of pricing plans to suit different needs. Whether you need just a few credits or want to invest in larger packages, there's an option available for everyone. With credits starting at affordable prices, users can quickly gain access to the platform and explore the features that undress AI has to offer. This flexibility makes the tool accessible for a wide audience.
High-Quality Image Results
One of the standout features of undress AI is its image quality. The platform ensures that all generated images are in full high definition. This means that users receive clear, detailed, and realistic results every time they use the service. The high-quality output is a crucial aspect of undress AI, as it enhances the overall user experience and ensures satisfaction.
Ethical Implications of Undress AI
The ethical concerns surrounding undress AI cannot be ignored. The ability to undress AI is a powerful tool, and its misuse can lead to privacy violations or harmful situations. It is crucial for users to engage with this technology responsibly and ethically, ensuring that it is not used to exploit or harm others. As with any powerful technology, ethical considerations should guide its usage.
Conclusion: The Impact of Undress AI
Undress AI is an innovative tool that opens up new possibilities in digital image manipulation. With its sophisticated algorithms and high-quality results, it’s clear why this technology is gaining popularity. However, like any powerful tool, it must be used responsibly. By understanding its capabilities and limitations, users can enjoy undress AI in a safe and ethical manner. As technology continues to evolve, it will be interesting to see how undress AI develops and what new features it will bring to the world of digital art and image processing.
2 notes
·
View notes
Text
Face Blur Technology in Public Surveillance: Balancing Privacy and Security
As surveillance technology continues to evolve, so do concerns about privacy. One solution that addresses both the need for public safety and individual privacy is face blur technology. This technology automatically obscures individuals’ faces in surveillance footage unless there’s a legitimate need for identification, offering a balance between security and personal data protection.
Why Do We Need Face Blur Technology?
Surveillance systems are increasingly used in public spaces, from streets and parks to malls and airports, where security cameras are deployed to monitor activities and prevent crime. However, the widespread collection of images from public spaces poses serious privacy risks. Personal data like facial images can be exploited if not properly protected. This is where face blur technology comes in. It reduces the chances of identity theft, unwarranted surveillance, and abuse of personal data by ensuring that identifiable information isn’t exposed unless necessary. Governments, businesses, and institutions implementing face blur technology are taking a step toward more responsible data handling while still benefiting from surveillance systems (Martinez et al., 2022).
Key Technologies Behind Face Blur
Face blur technology relies on several key technologies:
Computer Vision: This technology enables systems to detect human faces in images and videos. Using machine learning algorithms, cameras or software can recognize faces in real-time, making it possible to apply blurring instantly.
Real-life example: Google’s Street View uses face blur technology to automatically detect and blur faces of people captured in its 360-degree street imagery to protect their privacy.
Artificial Intelligence (AI): AI plays a crucial role in improving the accuracy of face detection and the efficiency of the blurring process. By training models on large datasets of human faces, AI-powered systems can differentiate between faces and non-facial objects, making the blurring process both accurate and fast (Tao et al., 2023).
Real-life example: Intel’s OpenVINO toolkit supports AI-powered face detection and blurring in real-time video streams. It is used in public surveillance systems in places like airports and transportation hubs to anonymize individuals while maintaining situational awareness for security teams.
Edge Computing: Modern surveillance systems equipped with edge computing process data locally on the camera or a nearby device rather than sending it to a distant data center. This reduces latency, allowing face blurring to be applied in real-time without lag.
Real-life example: Axis Communications’ AXIS Q1615-LE Mk III surveillance camera is equipped with edge computing capabilities. This allows for face blurring directly on the camera, reducing the need to send sensitive video footage to a central server for processing, enhancing privacy.
Encryption: Beyond face blur, encryption ensures that any data stored from surveillance cameras is protected from unauthorized access. Even if footage is accessed by someone without permission, the identity of individuals in the footage remains obscured.
Real-life example: Cisco Meraki MV smart cameras feature end-to-end encryption to secure video streams and stored footage. In conjunction with face blur technologies, these cameras offer enhanced privacy by protecting data from unauthorized access.
How Does the Technology Work?
The process of face blurring typically follows several steps:
Face Detection: AI-powered cameras or software scan the video feed to detect human faces.
Face Tracking: Once a face is detected, the system tracks its movement in real-time, ensuring the blur is applied dynamically as the person moves.
Face Obfuscation: The detected faces are then blurred or pixelated. This ensures that personal identification is not possible unless someone with the proper authorization has access to the raw footage.
Controlled Access: In many systems, access to the unblurred footage is restricted and requires legal or administrative permission, such as in the case of law enforcement investigations (Nguyen et al., 2023).
Real-life example: The Genetec Omnicast surveillance system is used in smart cities and integrates privacy-protecting features, including face blurring. Access to unblurred footage is strictly controlled, requiring multi-factor authentication for law enforcement and security personnel.
Real-Life Uses of Face Blur Technology
Face blur technology is being implemented in several key sectors:
Public Transportation Systems: Many modern train stations, subways, and airports have adopted face blur technology as part of their CCTV systems to protect the privacy of commuters. For instance, London's Heathrow Airport uses advanced video analytics with face blur to ensure footage meets GDPR compliance while enhancing security.
Retail Stores: Large retail chains, including Walmart, use face blur technology in their in-store cameras. This allows security teams to monitor activity and reduce theft while protecting the privacy of innocent customers.
Smart Cities: In Barcelona, Spain, a smart city initiative includes face blur technology to ensure privacy in public spaces while gathering data to improve city management and security. The smart cameras deployed in this project offer anonymized data to city officials, allowing them to monitor traffic, crowd control, and more without compromising individual identities.
Journalism and Humanitarian Work: Media organizations such as the BBC use face blurring technology in conflict zones or protests to protect the identities of vulnerable individuals. Additionally, NGOs employ similar technology in sensitive regions to prevent surveillance abuse by oppressive regimes.
Public Perception and Ethical Considerations
Public perception of surveillance technologies is a complex mix of support and concern. On one hand, people recognize the need for surveillance to enhance public safety, prevent crime, and even assist in emergencies. On the other hand, many are worried about mass surveillance, personal data privacy, and the potential for abuse by authorities or hackers.
By implementing face blur technology, institutions can address some of these concerns. Studies suggest that people are more comfortable with surveillance systems when privacy-preserving measures like face blur are in place. It demonstrates a commitment to privacy and reduces the likelihood of objections to the use of surveillance in public spaces (Zhang et al., 2021).
However, ethical challenges remain. The decision of when to unblur faces must be transparent and subject to clear guidelines, ensuring that this capability isn’t misused. In democratic societies, there is ongoing debate over how to strike a balance between security and privacy, and face blur technology offers a middle ground that respects individual rights while still maintaining public safety (Johnson & Singh, 2022).
Future of Face Blur Technology
As AI and machine learning continue to evolve, face blur technology will become more refined, offering enhanced accuracy in face detection and obfuscation. The future may also see advancements in customizing the level of blurring depending on context. For instance, higher levels of obfuscation could be applied in particularly sensitive areas, such as protests or political gatherings, to ensure that individuals' identities are protected (Chaudhary et al., 2023).
Face blur technology is also expected to integrate with broader privacy-enhancing technologies in surveillance systems, ensuring that even as surveillance expands, personal freedoms remain protected. Governments and businesses that embrace this technology are likely to be seen as leaders in ethical surveillance practices (Park et al., 2022).
Conclusion
The need for effective public surveillance is undeniable in today’s world, where security threats can arise at any time. However, the collection of facial images in public spaces raises significant privacy concerns. Face blur technology is a vital tool in addressing these issues, allowing for the balance between public safety and individual privacy. By leveraging AI, computer vision, and edge computing, face blur technology not only protects individual identities but also enhances public trust in surveillance systems.
References
Chaudhary, S., Patel, N., & Gupta, A. (2023). AI-enhanced privacy solutions for smart cities: Ethical considerations in urban surveillance. Journal of Smart City Innovation, 14(2), 99-112.
Johnson, M., & Singh, R. (2022). Ethical implications of face recognition in public spaces: Balancing privacy and security. Journal of Ethics and Technology, 18(1), 23-37.
Martinez, D., Loughlin, P., & Wei, X. (2022). Privacy-preserving techniques in public surveillance systems: A review. IEEE Transactions on Privacy and Data Security, 9(3), 154-171.
Nguyen, H., Wang, T., & Luo, J. (2023). Real-time face blurring for public surveillance: Challenges and innovations. International Journal of Surveillance Technology, 6(1), 78-89.
Park, S., Lee, H., & Kim, J. (2022). Privacy in smart cities: New technologies for anonymizing public surveillance data. Data Privacy Journal, 15(4), 45-61.
Tao, Z., Wang, Y., & Li, S. (2023). AI-driven face blurring in public surveillance: Technical challenges and future directions. Artificial Intelligence and Privacy, 8(2), 123-140.
Zhang, Y., Lee, S., & Roberts, J. (2021). Public attitudes toward surveillance technology and privacy protections. International Journal of Privacy and Data Protection, 7(4), 45-63.
2 notes
·
View notes
Text
The Rise of "Smart" Implants: How AI is Transforming Orthopedics from the Inside Out

Imagine a world where your artificial hip talks to you. Not literally, of course, but through a network of sensors and processors that monitor its performance, predict potential issues, and even adjust its settings in real time. This is the vision of "smart" implants, a cutting-edge field in orthopedics that promises to revolutionize the way we treat musculoskeletal conditions.
Beyond Metal and Plastic:
Traditionally, implants like joint replacements have been passive, inert devices. But "smart" implants are different. They are equipped with:
Sensors: These tiny sensors can monitor everything from joint movement and pressure to bone density and temperature.
Processors: These miniaturized computers analyze the data from the sensors and make informed decisions based on algorithms.
Actuators: These mechanisms can adjust the implant's settings, like changing the tension in a knee implant or stimulating bone growth around a hip replacement.
Benefits Beyond the Operating Room:
The potential benefits of "smart" implants are numerous:
Improved Outcomes: Real-time data allows for personalized adjustments to the implant, leading to quicker healing, better joint function, and a reduced risk of complications.
Predictive Maintenance: The implant can "talk" to your doctor, alerting them to potential problems before they occur, allowing for preventative interventions and avoiding painful and costly revision surgeries.
Remote Monitoring: Patients can be monitored remotely, reducing the need for frequent hospital visits and improving convenience.
Data-Driven Insights: The data collected from "smart" implants can inform future research and development, leading to even more advanced orthopedic treatments.
Challenges and Considerations:
While exciting, the development and integration of "smart" implants come with challenges:
Cost and Accessibility: These advanced technologies are expensive, and ensuring equitable access to them is crucial.
Battery Life: Powering these miniaturized devices within the body is a challenge, and research is ongoing to develop longer-lasting batteries.
Data Privacy and Security: Protecting patient data from unauthorized access and misuse is paramount.
Regulatory Landscape: Clear regulations and standards are needed to ensure the safety and efficacy of these devices.
The Future of Orthopedics:
Despite the challenges, the future of orthopedics is undoubtedly intertwined with "smart" implants. Continued research, development, and ethical considerations are vital to ensure that these technologies benefit everyone. By harnessing the power of AI and advanced engineering, we can move towards a future where orthopedic care is personalized, proactive, and ultimately, more effective for every patient.
Let's embrace the future of "smart" implants and pave the way for a healthier, more pain-free future for all!
#artificial intelligence#machine learning#deep learning#technology#robotics#orthopedic implants#orthopedics#surgery#hospital#patientcare#healthcare
2 notes
·
View notes
Text
How To Become Cybersecurity Expert: Scope, Skills, and Salary
In today's digitally interconnected world, it is of utmost importance to secure your company from online threats. Cybersecurity experts play a crucial role in achieving this goal. Their primary responsibility is to proactively identify and prevent potential attacks. They conduct scans and analyze network data to detect any weaknesses and dangers in networks, data centres, and software systems. Additionally, they ensure that hardware and software are always kept up-to-date.
In this article, we'll explore what a cybersecurity professional does, the skills they need, the career growth possibilities, and the typical salary. You can enhance your knowledge in this field by taking a cybersecurity certification online course to learn about modern information and system protection technologies.
What Does a Cybersecurity Specialist Do?
A cyber security specialist is essentially a guardian of computer networks and systems. Their primary mission is to shield these digital domains from a multitude of cyber threats while ensuring the confidentiality, integrity, and availability of critical data. Here are some key responsibilities of a cyber security specialist:
Identifying Vulnerabilities: Their first task is to hunt down and fix security weaknesses in networks, data centres, and software systems. Think of them as the digital detectives who uncover potential entry points for cybercriminals.
Implementing Security Controls: Cyber security specialists employ a variety of security measures such as firewalls, encryption, and multi-factor authentication to fortify digital assets against potential attacks. These measures act as digital barriers, thwarting unauthorized access.
Monitoring Activity: They keep a vigilant eye on network and system activity, looking for any signs of intrusion or suspicious behaviour. This proactive approach enables them to respond swiftly to potential threats.
Responding to Incidents: In the event of a cyberattack, cyber security specialists jump into action. They react swiftly, notifying law enforcement, restoring backups, and communicating with the affected parties through public statements.
Keeping Up with Trends: The ever-evolving nature of cyber threats means that cyber security specialists must stay updated on the latest trends and technologies in the field. Being one step ahead is essential in this game.
Depending on their specialization and level of expertise, cyber security specialists may have different job titles, including:
Cybersecurity Analyst: Responsible for planning, implementing, and monitoring security strategies within an organization.
Cybersecurity Engineer: Designing and building systems to safeguard digital information.
Cybersecurity Architect: Developing and overseeing an organization's entire cyber security strategy.
Cybersecurity Manager: Formulating and implementing security policies while managing security teams.
Penetration Tester: Simulating cyberattacks to identify security weaknesses and providing recommendations.
Chief Information Security Officer: Leading an organization's cybersecurity efforts and collaborating with other executives.
Information Security Crime Investigator: Reviewing evidence to determine if cybercrimes have occurred and assisting law enforcement in apprehending suspects.
Cybersecurity Consultant: Advising organizations on how to identify and mitigate network risks.
Cybersecurity Specialist Skills
Cybersecurity specialist requirements include a blend of technical and soft skills. Here's a breakdown:
Technical Skills:
Network Security: The ability to protect networks from unauthorized access, misuse, or disruption is a foundational skill.
Cryptography: Understanding mathematical techniques to encrypt and decrypt data is essential for securing sensitive information.
Risk Management: Assessing and mitigating potential threats to an organization's information systems is crucial to avoid vulnerabilities.
Cybersecurity Tools and Technologies: Proficiency in using various software and hardware tools for tasks like scanning, testing, and auditing is vital.
Soft Skills:
Communication Skills: Effectively conveying security concepts and findings to both technical and non-technical audiences is essential for collaboration and understanding.
Problem-Solving Skills: The ability to analyze complex situations and find effective solutions is key to navigating the ever-changing cyber landscape.
Critical Thinking Skills: Evaluating information objectively and logically helps make informed decisions in high-pressure situations.
Strategic Thinking Skills: Planning and anticipating future scenarios enable proactive security measures.
How to Become a Cybersecurity Specialist?
Entering the field of cyber security can be achieved through various avenues. Here are some common paths:
Formal Education: Enroll in college or university programs that offer degrees or diplomas in cyber security or related fields. This provides a solid academic foundation.
Self-Study and Certification: Study independently using online resources and obtain relevant certifications to showcase your knowledge and skills. This self-driven approach allows flexibility.
Volunteering and Training: Seek opportunities to volunteer or join organizations offering cybersecurity training programs or internships. Practical experience is invaluable.
Entrepreneurship: Consider starting your own cybersecurity business or joining a team of experts. This path offers autonomy and the chance to work on diverse projects.
What Certifications are Needed for Cybersecurity?
Cyber security certifications are vital for validating your expertise and commitment to the field. They also provide a structured path for acquiring the necessary skills and knowledge. Here are some common certifications:
Certified Cybersecurity Expert™: Ideal for entry-level professionals, this certification covers the fundamentals of cyber security, including network security, threat management, and cryptography.
Certified Information Security Executive™: Designed for experienced professionals, it delves into advanced aspects like security architecture, risk management, and governance.
Certified White Hat Hacker™: Specializing in offensive security, this certification covers ethical hacking techniques, including penetration testing, vulnerability assessment, and malware analysis.
Salary Expectations for Cybersecurity Specialists
The salary of a cyber security specialist can vary based on factors such as location, experience, education, and certifications. However, the average salary in the United States is approximately $117,419 per year. Experienced professionals can command even higher earnings, while those with advanced degrees or certifications enjoy enhanced job prospects.
In conclusion, cyber security is a dynamic and rewarding field that offers a wide array of career opportunities. By understanding the role, acquiring the necessary skills and certifications, and exploring salary prospects, you can embark on a fulfilling journey to become a cybersecurity specialist. Online cyber security certification courses are readily available to help you gain knowledge and skills in modern information and system protection technologies. With dedication and the right tools, you can help safeguard the digital world from cyber threats and play a crucial role in our increasingly digital lives.
If you're interested in pursuing cyber security or blockchain security certifications with a focus on emerging technologies like blockchain, consider exploring the offerings provided by the Blockchain Council. The Blockchain Council is a respected consortium of subject matter experts and enthusiasts dedicated to advancing blockchain research and development, exploring use cases and products, and disseminating knowledge for a better world.
2 notes
·
View notes
Text
How Can You Confirmed With 꽁머니 즉시 지급?

A toto site is a safe playground that allows you to place your bets without any fears. Its eat and run verification software uses 14 high-end methods to ensure reliability and quality. It will also protect you from fraudulent activities. A toto site is a great option for beginners who are new to online gambling. It provides a low stakes environment for practice and round-the-clock customer support. The toto site chat room is available twenty-four hours a day. This allows you to chat with other players and make new friends. You can play games together or ask questions about the latest games. There are also forums where you can discuss the latest game updates. In addition, you can use telegram to contact customer support.
Another security measure on toto sites is the oppous for play game feature. This will prevent unauthorized users from using your account to access your personal information or financial details. This feature will also allow you to control who can access your account. It will also block certain types of malware and spyware on your computer. The toto website is a good resource for finding information about different online casinos and gambling platforms. It also provides helpful tips and strategies for maximizing your winnings.
Private toto sites and casinos are a great way to keep your personal information safe and your 꽁머니 즉시 지급 anonymous. They are usually much safer than traditional online casinos and offer more security features than ever before. They are also easier to use, and they typically have better customer service teams. The toto site has a wide variety of games for its members to enjoy. In addition to its many games, the site offers a chat room where you can chat with other players and make new friends. The toto site is free to join, and there are no time limits or restrictions on how long you can play.
Toto sites also prioritize user safety by requiring their operators to verify the identity of their customers. This verification process is designed to ensure that only genuine individuals participate in the betting ecosystem. In addition, major toto sites are registered with recognized gambling authorities and have secure registration information in the footer of their websites.
youtube
In addition to ensuring the safety of its customers, toto sites promote fairness and transparency. They encourage their operators to abide by local laws and Company regulations regarding the protection of personal information. They also strive to develop sensible business activities that are socially acceptable and sustain sound normal relationships with political organizations and governmental administrations. In this way, they aim to achieve a win-win situation for both customers and their business partners. The toto site will not tolerate any illegal or unethical behavior by its operators. Its employees must abide by the laws and societal rules of their country and region, as well as the international norms that apply to their work. In doing so, they can contribute to the prosperity and welfare of the community.
2 notes
·
View notes
Text
Does anyone besides Musk and his team know how sensitive data is being handled, stored, safeguarded and/or used? Does anyone know if the data is being maintained with the same stringent standards that real government contractors must meet and abide by? Are there safeguards to prevent manipulation of this data? Does anyone know whether the DOGE team are adding "back doors" to government computer systems to allow for future unauthorized access? Is there anything preventing them from selling data to foreign governments and other malevolent actors?


‼️‼️‼️‼️‼️
792 notes
·
View notes
Text
Smart Strategies for Secure IT Asset Disposition

Protecting Data, Ensuring Compliance, and Promoting Sustainability
In a digital-first world, organizations deal with an ever-increasing volume of IT assets servers, computers, hard drives, networking equipment, and more. When these assets reach end-of-life, the way you dispose of them can impact your data security, regulatory compliance, and environmental footprint. This is where smart IT asset disposition (ITAD) becomes critical.
At Techazar, we help businesses across India adopt secure and sustainable IT asset disposition strategies. Here's how your company can do the same.
1. Adopt Industry-Standard Data Destruction
Before any device is decommissioned, ensure all data is completely and irreversibly erased. Use certified data sanitization methods like NIST 800-88 and DoD 5220.22-M to meet international security benchmarks.
Why it's important:
Prevents unauthorized access and data leaks
Supports ISO 27001, GDPR, and other compliance needs
Protects business reputation and client trust
2. Partner with Certified ITAD and E-Waste Experts
Working with a CPCB-authorized, ISO-certified e-waste company ensures responsible handling of your assets. Certified vendors like Techazar provide end-to-end ITAD services, including documentation and secure recycling.
Advantages:
Audit-ready certificate of destruction
Legal compliance with environmental standards
Responsible e-waste recycling and material recovery
3. Maintain Accurate IT Asset Inventory
A complete and regularly updated inventory of your IT equipment helps track the lifecycle of each asset. This ensures that no device is forgotten or disposed of improperly.
Benefits include:
Efficient asset management
Reduced risk of data loss
Simplified audits and reporting
4. Choose Between On-Site and Off-Site Wiping
Secure data wiping can be done at your location (on-site) or at a certified facility (off-site). Choose based on your security policies and logistical needs.
Ideal for:
Enterprises handling sensitive data
Government and regulated industries
Remote or multi-location operations
5. Prioritize Eco-Friendly E-Waste Recycling
ITAD isn’t complete without environmentally responsible recycling. Dispose of electronic waste through processes that reduce landfill contributions and recover valuable resources such as rare earth metals and copper.
Sustainability benefits:
Aligns with ESG goals
Minimizes environmental damage
Promotes circular economy principles
6. Demand a Certificate of Destruction
After disposal, always ask for a Certificate of Destruction (CoD). This document serves as official proof that your devices were securely wiped and disposed of in line with applicable laws.
Why it matters:
Legal protection in case of data audits
Evidence of compliance for stakeholders
Peace of mind for IT and compliance teams
7. Train Employees on ITAD Policies
Your team is your first line of defense. Provide regular training to IT staff and asset managers on the latest ITAD best practices, data security protocols, and internal policies.
Final Thoughts
Effective IT asset disposition is more than an operational necessity; it’s a strategic function that supports data security, regulatory compliance, and sustainability initiatives. By adopting smart ITAD strategies, businesses can safeguard their information, reduce environmental impact, and stay legally compliant.
For complete ITAD services across India, visit Techazar.in
#SecureITDisposal#ITAssetDisposition#EwasteManagement#Techazar#ITADSolutions#EwasteRecycling#CertifiedEwasteCompany#ITDisposalCompany#DataWiping#NISTCompliant#DoDStandard#SustainableEwaste#RecycleITAssets#ElectronicRecycling#CPCBCertified
0 notes
Text
Simplifying Digital Security and Access with Trusted Software Keys
In a time when digital convenience is important for both work and play, having easy access to licensed software is not just a nice thing to have; it's a must. Cybersecurity technologies and operating systems are becoming essential parts of digital safety and efficiency. A valid Windows 11 key not only allows for legal activation but also guarantees that you will get all of the updates and security fixes you need. This article talks about how important it is to get digital product keys from real sources for both performance and safety.
Understanding the Role of a Genuine Windows 11 Key
Real software licenses are important for keeping your system stable and preventing performance problems that might happen with pirated copies. A real Windows 11 key gives you access to advanced features, security upgrades, and complete compatibility with future program integrations. When consumers depend on unlicensed systems, they often run into problems like limited functionalities and being more open to infection. If you buy a real key, you'll get a better user experience, better security, and official support. It's a simple approach to keep your data and gadget running well for a long time.
The Risks of Using Unauthorized Operating Systems
Using unlicensed operating systems may seem like a good way to save money at first, but it may have major long-term effects. When a Windows 11 key isn't real, devices may get constant alarms, have fewer customization choices, and even risk losing data. Also, bad people often go for non-authentic computers since they don't obtain the right upgrades. In addition to technological issues, there are also legal risks, particularly for commercial users. A licensed operating system is still the safest and most dependable way to operate without interruptions and keep your data protected.
Digital Security: Why McAfee Key is Essential for Protection
As digital dangers become worse, it's more critical than ever to have good antivirus protection. A certified McAfee key gives you full protection against viruses, malware, phishing attempts, and ransomware assaults. Licensed McAfee is better than free or pirated security software since it gives you real-time updates and comprehensive scanning features that are needed to find new threats. A certified antivirus program is an important safeguard in a world where digital fingerprints are always being attacked. This protection is very important when sensitive information like bank records, personal papers, or private business documents is in danger.
Enhancing Device Safety with a McAfee Key Subscription
When security software is always up to date and works properly, it works best. Users who don't have a licensed McAfee key may not be able to utilize all of the features, find threats more slowly, or get the latest firewall updates. Protection based on a subscription gives you peace of mind by making regular upgrades and quickly finding new cyber dangers. This layer of protection is a must for each person who keeps important data on their personal or professional gadgets. Activating a legitimate McAfee license now not best makes matters safer, but it additionally makes human beings much more likely to trust a further when they use the net for such things as shopping, browsing, or exchanging documents.
Conclusion
Digital licenses are important for more than just installation; they also safeguard you, help you be more productive, and provide you peace of mind. Real product keys are necessary to turn on a trustworthy operating system or protect a gadget from contemporary cyber threats. Key-Soft.pl/en is a simple method to get a legitimate Windows 11 key and a McAfee key for those who want real software solutions. These keys are both essential for keeping your virtual sports secure and running smoothly. In the modern, ever-changing digital world, choosing certified merchandise from an identified dealer makes sure you have access to all of the features, that they work with no troubles, and that you get great safety.
0 notes
Text
Troubleshooting Common Issues Through PLDTHomeWiFiSettings

Dealing with internet slowdowns or connectivity issues can be frustrating, especially when you rely heavily on WiFi for work, streaming, and daily communication. Fortunately, many common problems can be resolved using pldthomewifisettings. This guide will walk you through practical troubleshooting tips and tricks using your PLDT router's admin panel.
Understanding PLDTHomeWiFiSettings
The pldthomewifisettings portal is your gateway to diagnosing and solving most network issues at home. From checking signal strength to rebooting your system remotely, it offers a variety of tools to enhance your internet experience.
How to Access PLDTHomeWiFiSettings
Before troubleshooting, you’ll need to access the settings:
Connect your phone or computer to the PLDT Home WiFi.
Open a web browser and type 192.168.1.1 or 192.168.0.1.
Enter login credentials—usually "admin" and "1234" (or "adminpldt" with a specific password).
You’ll now see the pldthomewifisettings dashboard.
Once inside, you’re ready to start troubleshooting.
Problem 1: Slow Internet Speed
If your internet seems slower than expected:
Go to Status > WAN to check the real-time speed.
Run a speed test from your browser and compare it with your subscribed plan.
Use QoS Settings to prioritize work-related devices or apps.
Reduce the number of connected devices by checking the Client List.
Through pldthomewifisettings, you can quickly allocate bandwidth to where it matters most.
Problem 2: Frequent Disconnections
A common issue with wireless connections is frequent drops. Try the following:
Change the WiFi Channel under Wireless Settings. Avoid crowded channels like 1 or 6.
Switch from 2.4GHz to 5GHz if supported. It’s faster and less prone to interference.
Ensure firmware is updated via System > Firmware Upgrade.
If none of these fixes work, a factory reset through pldthomewifisettings might be necessary.
Problem 3: Unauthorized Users on the Network
Are you noticing unfamiliar devices?
Navigate to the Client List in your dashboard.
Block unknown devices using MAC Filtering.
Change your WiFi password under Wireless > Security and re-authenticate trusted devices.
Regularly monitoring your pldthomewifisettings can help you catch freeloaders before they eat up your bandwidth.
Problem 4: Can’t Connect to WiFi
Sometimes your device might not connect at all:
Restart your router using System > Reboot.
Check if the WiFi signal is hidden. Go to Wireless Settings and make sure SSID broadcast is enabled.
Ensure the device isn’t blocked under MAC Filtering.
This is a common situation easily resolved by checking settings via pldthomewifisettings.
Problem 5: WiFi Signal Weak in Certain Areas
Dead zones in your house?
Try changing the transmission power from “Low” to “High” under Wireless > Advanced Settings.
Reposition your router centrally in your home.
Add a WiFi extender or Mesh system and link it via LAN cable.
While pldthomewifisettings can help optimize range, hardware limitations may also need to be addressed.
Problem 6: Can’t Log In to PLDTHomeWiFiSettings
If you can’t even access the admin panel:
Check the IP address. It should be 192.168.1.1 or 192.168.0.1.
Make sure you're connected to the PLDT WiFi, not mobile data.
Reset the router to factory settings using the small reset button at the back.
Access to pldthomewifisettings is crucial for all troubleshooting, so this step is foundational.
Problem 7: Port Forwarding Not Working
Need to open ports for gaming or remote access?
Navigate to NAT > Port Forwarding.
Input the local IP, start/end port, and protocol.
Save and reboot the router.
If port forwarding doesn’t work even after setup, check with PLDT support—some accounts are on CGNAT which restricts this function.
Preventive Maintenance Tips
Log into your pldthomewifisettings weekly to monitor devices.
Change your password monthly.
Keep firmware updated.
Avoid overloading your network with too many devices.
Preventive maintenance reduces the frequency of technical problems and improves long-term performance.
Conclusion
When problems arise with your internet, don’t panic. Many issues—from speed concerns to unknown users—can be resolved by exploring your pldthomewifisettings. By taking the time to understand the control panel, you empower yourself to maintain a fast, secure, and stable network connection without always needing technical support.
FAQs on PLDTHomeWiFiSettings Troubleshooting
Q1. What should I do if my PLDT WiFi keeps disconnecting? Ans. Check for channel interference, update firmware, and limit the number of connected devices using pldthomewifisettings.
Q2. Can I remove a device from my WiFi using PLDTHomeWiFiSettings? Ans. Yes, go to the device list, find the suspicious device, and block it via MAC filtering.
Q3. What if I forget my PLDTHomeWiFi admin password? Ans. You can reset the router to factory settings and log in using default credentials, then reset the password again.
0 notes
Text
Blockchain and BIM Data Security

The Architecture, Engineering, and Construction (AEC) industry is rapidly adopting Building Information Modeling (BIM) for enhanced project collaboration and efficiency. However, as BIM involves sharing vast amounts of sensitive data across multiple stakeholders, security concerns have become a significant challenge. Blockchain technology presents a revolutionary solution to safeguard BIM data, ensuring transparency, security, and trust in the digital construction ecosystem.
What is Blockchain?
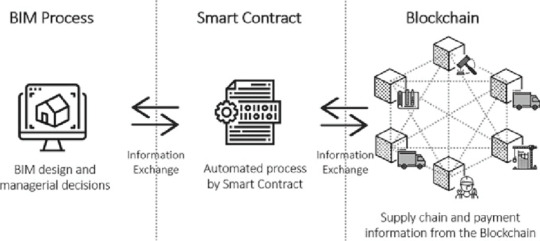
Blockchain is a decentralized digital ledger that operates across a network of computers, ensuring secure and transparent data management. It enables smart contracts, automating transactions without intermediaries. Each new entry, or "block," is verified by the network before being permanently added to an unbreakable chain of records.
Protected by advanced cryptographic algorithms, blockchain is highly resistant to hacking. Since every block is immutably linked to the previous one, altering any record would require modifying the entire chain—an almost impossible feat. This structure not only enhances security but also allows for seamless traceability, making blockchain a trusted solution for safeguarding digital information.
BIM Data Security Challenges

BIM data is shared among architects, engineers, contractors, and clients throughout a project’s lifecycle. The key security challenges include:
Data Integrity: Unauthorized modifications or tampering with BIM data can lead to costly errors and project delays.
Access Control: Multiple stakeholders require different access levels, making it crucial to manage permissions effectively.
Cyber Threats: BIM platforms are vulnerable to hacking, data breaches, and ransomware attacks.
Data Ownership & Authentication: Establishing data ownership and verifying authenticity are complex in collaborative environments.
How Blockchain Enhances BIM Data Security

Blockchain, a decentralized and tamper-proof digital ledger, addresses these challenges effectively by offering:
1. Immutable Data Storage
Blockchain ensures data integrity by storing BIM records in a decentralized ledger. Once recorded, data cannot be altered or deleted without consensus, preventing unauthorized modifications.
2. Enhanced Access Control & Authentication
With blockchain-based smart contracts, stakeholders can define access permissions for different project participants. Only authorized personnel can modify specific elements of the BIM model, reducing unauthorized changes and data breaches.
3. Transparent and Secure Collaboration
Every transaction within the BIM model is timestamped and recorded on the blockchain. This fosters transparency and accountability, making dispute resolution easier and eliminating fraud.
4. Protection Against Cyber Threats
Since blockchain operates on a decentralized network, hacking a single node does not compromise the entire system. This significantly enhances security against cyber threats and ransomware attacks.
5. Data Ownership and Provenance
Blockchain enables digital signatures and cryptographic verification, ensuring clear data ownership. Every modification is tracked, providing an auditable history of changes, which is crucial for compliance and legal documentation.
Real-World Applications of Blockchain in BIM
Several companies and governments are exploring blockchain integration with BIM for secure construction data management. Some notable applications include:
Smart Contracts for Automated Payments: Payments are released automatically based on predefined project milestones recorded in BIM.
Decentralized Data Storage: BIM files are stored securely on blockchain-based cloud systems, reducing reliance on centralized servers.
Regulatory Compliance & Audit Trails: Authorities can verify project data integrity and compliance using blockchain records.
The fusion of Blockchain and BIM is revolutionizing data security in the AEC industry. By ensuring data integrity, secure access control, and protection against cyber threats, blockchain technology enhances trust and efficiency in construction projects. As BIM adoption grows, integrating blockchain will become essential for safeguarding digital construction workflows and ensuring a more secure future for the industry.
Are you ready to enhance your BIM data security with blockchain? Stay ahead of the curve and explore the future of secure digital construction!
Are you looking for an online BIM course in Kochi, Kerala? We offer both online and offline BIM courses in Kerala to help civil engineers, architects, and interior designers build a strong foundation in BIM. Whether you're a beginner or an experienced professional, our expert-led training will equip you with the skills needed to excel in the industry.
Start your BIM journey with Anita BIM Solutions today and take your career to the next level!
0 notes
Text
Transforming Highways with AI-Based Traffic Management Systems
As our highways grow busier and more complex, the demand for smarter, more efficient traffic control is undeniable. Traditional traffic enforcement systems, dependent on human intervention, are often reactive, inconsistent, and limited in scope. Enter the AI-based traffic management system—a transformative technology that combines real-time analytics, automation, and machine learning to revolutionize how we manage and monitor highway traffic.
This blog explores how AI is redefining traffic management through vehicle detection, violation enforcement, and traffic classification, with real-world applications and insights to understand its growing importance in building safer and smarter roads.
The Core of AI-Based Traffic Monitoring
At the heart of an AI-based traffic management system lies its ability to collect and process vast volumes of real-time data. Equipped with cameras, sensors, and AI algorithms, these systems can identify, interpret, and act upon various traffic conditions and violations in real time.
From detecting license plates to classifying vehicles and tracking violations, AI systems offer unmatched speed and precision. Let’s break down the three core components powering this transformation:
1. Vehicle Make, Model, and Number Plate Detection
One of the most essential features of modern AI traffic management is vehicle identification. Advanced computer vision algorithms now allow for:
Vehicle Make & Model Recognition: Detects and categorizes vehicles based on appearance using trained AI models.
Number Plate Detection (ANPR): Reads license plates using Automatic Number Plate Recognition (ANPR) technology.
This technology is crucial for highway safety and enforcement. Authorities can:
Track Stolen Vehicles: Real-time tracking makes it easier to recover stolen cars.
Ensure Speed Compliance: By linking vehicle IDs with speed detection, violators can be automatically penalized.
Enhance Border Security: Enables region-wise data access and movement patterns of vehicles.
2. Real-Time Violation Detection
Road safety heavily depends on the ability to detect violations and respond swiftly. With AI-based traffic management systems, violations are detected automatically and enforcement actions are taken instantly, reducing the burden on human officers.
Common Violations Detected:
Triple Riding: AI identifies motorcycles carrying more than two passengers, a major road hazard.
No Helmet Detection: Computer vision tracks helmet usage to ensure compliance.
Over Speeding: Speed detection cameras linked to AI algorithms monitor speed limits.
No Seatbelt: Identifies drivers and passengers not wearing seatbelts, especially in high-speed zones.
Wrong Direction: Detects vehicles traveling against traffic flow to prevent collisions.
Wrong Lane Use: Flags unauthorized lane usage (e.g., bus or emergency lanes).
Banned Vehicles: Detects commercial or high-emission vehicles in restricted zones.
No Parking/Stalled Vehicle: Identifies illegal parking or breakdowns to prevent traffic build-up.
The AI system’s ability to issue digital challans (fines), alert authorities, or guide law enforcement to violators ensures more consistent and efficient enforcement.
3. Automatic Traffic Counting and Classification (ATCC)
Beyond enforcement, highway authorities need to understand traffic behavior and infrastructure needs. Automatic Traffic Counting and Classification (ATCC) enables real-time monitoring and segmentation of traffic by vehicle type, time, and location.
Vehicle Classifications Typically Tracked:
2-Wheelers (Motorcycles)
3-Wheelers (Auto-rickshaws)
4-Wheelers (Cars, SUVs)
Light Commercial Vehicles (4/6-Tire)
Mini Light Commercial Vehicles
2 to 6-Axle Trucks
Heavy Commercial Machinery (HCM)
Tractors, Goods Auto, Buses, Mini Buses
Cycles and Light Goods Vehicles (LGV)
ATCC data enables:
Traffic Flow Analysis: Understand volume trends across time slots.
Infrastructure Planning: Identify needs for road expansions or maintenance.
Smart City Integration: Coordinate with broader intelligent transport systems.
Optimized Toll Collection: Dynamic pricing based on vehicle class and time.
Case Study: South Korea’s AI-Driven Highway Monitoring
South Korea has implemented an integrated AI-based traffic management system across major highways. The system combines ANPR, ATCC, and violation detection into a unified control center.
Results:
20% reduction in road accidents due to automated enforcement.
30% improvement in emergency response times.
Real-time updates for commuters through integrated apps.
Significant fuel savings from smoother traffic flow.
This comprehensive approach highlights the power of combining multiple AI capabilities into one intelligent system.
Benefits of AI Traffic Management on Highways
1. Enhanced Road Safety
AI proactively detects and prevents risky behavior, leading to fewer accidents.
2. Reduced Congestion
Traffic patterns can be optimized dynamically, minimizing bottlenecks.
3. Data-Driven Decision-Making
Authorities receive rich, real-time data to inform planning and investments.
4. Operational Efficiency
Reduces dependency on manual monitoring, freeing up human resources.
5. Environmental Impact
Fewer traffic jams = less fuel burned and lower emissions.
6. Smart Infrastructure Growth
Lays the groundwork for autonomous vehicles and future mobility solutions.
The Future of AI-Based Traffic Management Systems
The next generation of AI traffic management will be even more advanced:
Predictive Analytics: AI will forecast congestion and reroute traffic in advance.
Autonomous Enforcement: Drones and mobile AI units will handle dynamic situations.
Vehicle-to-Infrastructure (V2I) Communication: AI systems will connect with smart vehicles to share real-time updates.
AI + IoT Integration: IoT sensors embedded in roads will feed AI models with infrastructure-level data.
As smart cities evolve, these systems will become central to urban mobility.
Challenges and Considerations
Despite the benefits, certain challenges must be addressed:
Privacy Concerns: Data collection must follow ethical and legal frameworks.
High Initial Investment: Infrastructure setup is capital-intensive.
System Maintenance: Requires regular updates, calibration, and power backups.
False Positives: AI models need to be well-trained to avoid misidentification.
Conclusion: The AI Highway Revolution Has Begun
An AI-based traffic management system is not just a futuristic concept—it is actively reshaping how highways function. From identifying violations and classifying vehicles to enabling informed infrastructure decisions, AI is making highways safer, smarter, and more sustainable.
As we move toward a future of autonomous transport and intelligent cities, these technologies will become foundational. For governments, city planners, and law enforcement agencies, adopting AI traffic management isn’t just a tech upgrade—it’s a necessity for the next era of mobility.
0 notes
Text
The Future of Secure Networking: Why SASE Is a Game-Changer
In today’s fast-paced digital environment, businesses face the challenge of managing secure and seamless connectivity for an increasingly distributed workforce. As remote work, cloud computing, and mobile access become the norm, legacy network architectures struggle to keep up. That’s why Secure Access Service Edge, or SASE, is quickly gaining traction as a next-generation solution for modern enterprises.
What Is SASE?
SASE is a cloud-native architecture that converges multiple networking and security functions into a single, unified service. It integrates tools such as:
Software-defined wide area networking (SD-WAN)
Firewall-as-a-service (FWaaS)
Secure Web Gateway (SWG)
Cloud Access Security Broker (CASB)
Zero Trust Network Access (ZTNA)
This integrated model allows businesses to enforce security policies and manage access control across all users, devices, and applications — regardless of their location.
Why SASE Matters for Modern Enterprises
The traditional hub-and-spoke network model routes all traffic through a central data center. While this approach was effective in the past, it creates unnecessary latency and bottlenecks in today’s cloud-first world. SASE offers a decentralized solution, providing direct, secure access to cloud applications while maintaining strong security controls.
For enterprises aiming for comprehensive modernization, adopting a secure network transformation strategy powered by SASE can lead to:
Improved performance and lower latency
Enhanced visibility and control over data access
Better scalability and simplified network management
Reduced security risks through zero-trust enforcement
How Tata Communications Delivers a Trusted SASE Framework
Tata Communications provides an end-to-end SASE solution that enables organizations to securely connect users to applications, no matter where they are. The architecture is built with performance, policy enforcement, and scalability in mind — aligning with business needs as they evolve.
Its model incorporates zero trust principles, meaning no user or device is trusted by default. Every access attempt is verified in real time using identity, device posture, and context, helping to prevent unauthorized access and data breaches.
By adopting SASE through Tata Communications, businesses can unify their security stack while optimizing user experience — making it a strategic investment for any digital transformation initiative.
Conclusion
As businesses continue to embrace hybrid work, multi-cloud environments, and remote access, the need for a modern, secure, and flexible network becomes critical. SASE is not just a trend — it’s the future of enterprise networking and security. By integrating security at the edge and delivering policy-based access through the cloud, it empowers organizations to be more agile, resilient, and secure.
If you're planning to overhaul your IT infrastructure or strengthen cloud access, now is the time to explore SASE as a cornerstone of your transformation strategy.
0 notes